mirror of
https://codeberg.org/forgejo/forgejo.git
synced 2025-02-22 22:26:26 +00:00
Backport #22850
Fixes: #22843
### Cause:
affdd40296/services/repository/files/content.go (L161)
Previously, we did not escape the **"%"** that might be in "treePath"
when call "url.parse()".
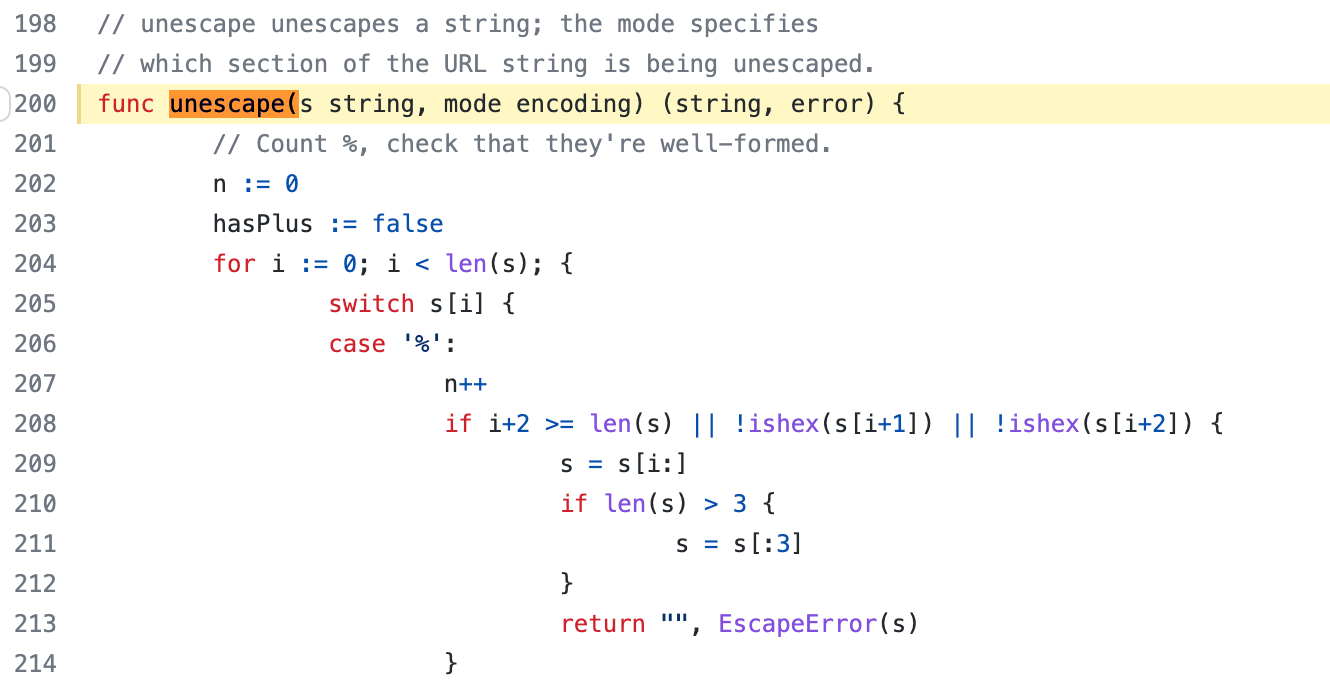
This function will check whether "%" is the beginning of an escape
character. Obviously, the "%" in the example (hello%mother.txt) is not
that. So, the function will return a error.
### Solution:
We can escape "treePath" by call "url.PathEscape()" function firstly.
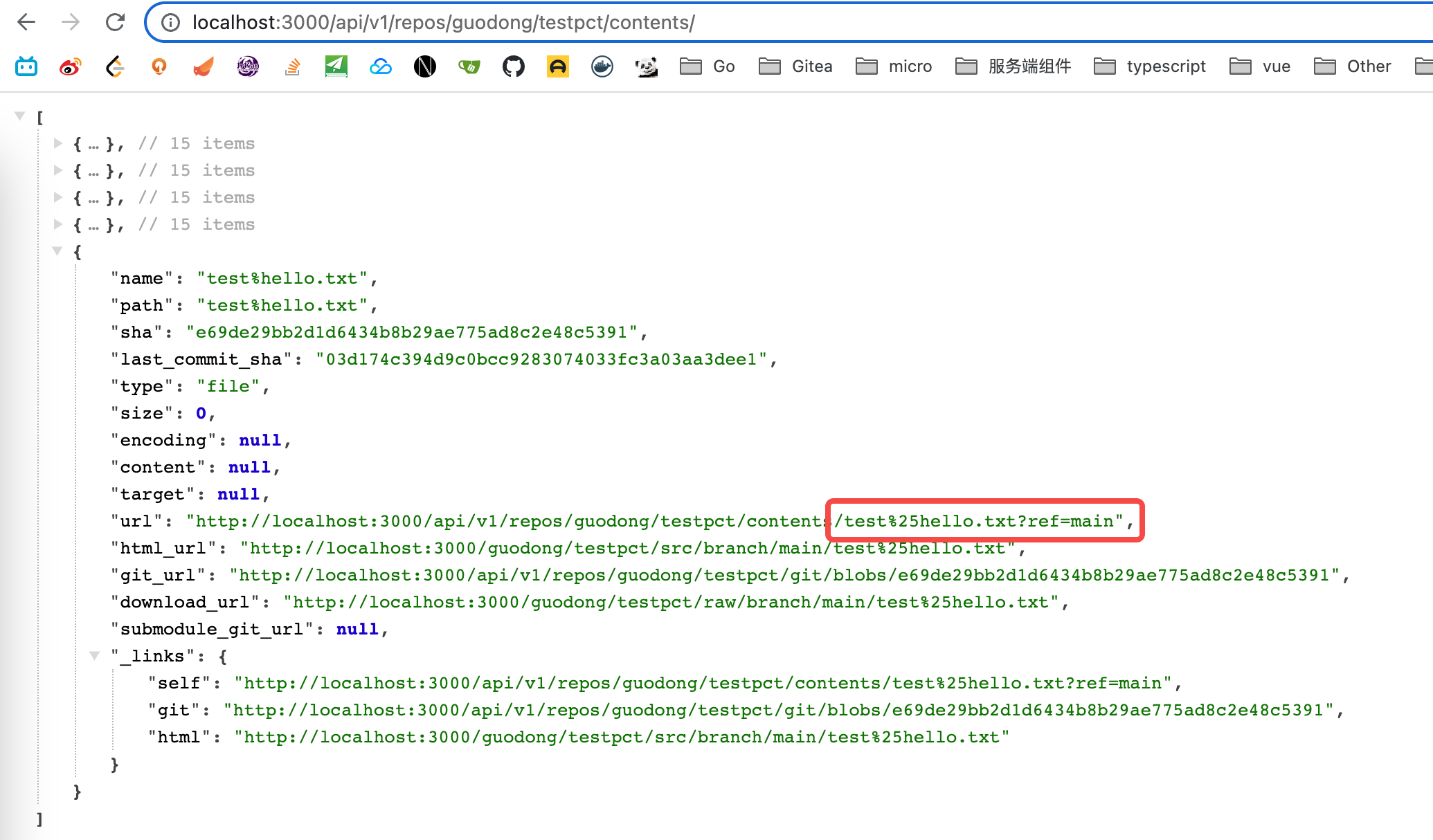
### Screenshot:
Signed-off-by: Andrew Thornton <art27@cantab.net>
Co-authored-by: sillyguodong <33891828+sillyguodong@users.noreply.github.com>
Co-authored-by: Andrew Thornton <art27@cantab.net>
This commit is contained in:
parent
8fa419c4c1
commit
43d1183f67
2 changed files with 7 additions and 6 deletions
|
|
@ -5,7 +5,6 @@
|
|||
package lfs
|
||||
|
||||
import (
|
||||
"fmt"
|
||||
"net/url"
|
||||
"os"
|
||||
"path"
|
||||
|
|
@ -13,6 +12,7 @@ import (
|
|||
"strings"
|
||||
|
||||
"code.gitea.io/gitea/modules/log"
|
||||
"code.gitea.io/gitea/modules/util"
|
||||
)
|
||||
|
||||
// DetermineEndpoint determines an endpoint from the clone url or uses the specified LFS url.
|
||||
|
|
@ -96,7 +96,7 @@ func endpointFromLocalPath(path string) *url.URL {
|
|||
return nil
|
||||
}
|
||||
|
||||
path = fmt.Sprintf("file://%s%s", slash, filepath.ToSlash(path))
|
||||
path = "file://" + slash + util.PathEscapeSegments(filepath.ToSlash(path))
|
||||
|
||||
u, _ := url.Parse(path)
|
||||
|
||||
|
|
|
|||
|
|
@ -16,6 +16,7 @@ import (
|
|||
"code.gitea.io/gitea/modules/git"
|
||||
"code.gitea.io/gitea/modules/setting"
|
||||
api "code.gitea.io/gitea/modules/structs"
|
||||
"code.gitea.io/gitea/modules/util"
|
||||
)
|
||||
|
||||
// ContentType repo content type
|
||||
|
|
@ -159,7 +160,7 @@ func GetContents(ctx context.Context, repo *repo_model.Repository, treePath, ref
|
|||
return nil, fmt.Errorf("no commit found for the ref [ref: %s]", ref)
|
||||
}
|
||||
|
||||
selfURL, err := url.Parse(fmt.Sprintf("%s/contents/%s?ref=%s", repo.APIURL(), treePath, origRef))
|
||||
selfURL, err := url.Parse(repo.APIURL() + "/contents/" + util.PathEscapeSegments(treePath) + "?ref=" + url.QueryEscape(origRef))
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
|
@ -218,7 +219,7 @@ func GetContents(ctx context.Context, repo *repo_model.Repository, treePath, ref
|
|||
}
|
||||
// Handle links
|
||||
if entry.IsRegular() || entry.IsLink() {
|
||||
downloadURL, err := url.Parse(fmt.Sprintf("%s/raw/%s/%s/%s", repo.HTMLURL(), refType, ref, treePath))
|
||||
downloadURL, err := url.Parse(repo.HTMLURL() + "/raw/" + url.PathEscape(string(refType)) + "/" + util.PathEscapeSegments(ref) + "/" + util.PathEscapeSegments(treePath))
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
|
@ -226,7 +227,7 @@ func GetContents(ctx context.Context, repo *repo_model.Repository, treePath, ref
|
|||
contentsResponse.DownloadURL = &downloadURLString
|
||||
}
|
||||
if !entry.IsSubModule() {
|
||||
htmlURL, err := url.Parse(fmt.Sprintf("%s/src/%s/%s/%s", repo.HTMLURL(), refType, ref, treePath))
|
||||
htmlURL, err := url.Parse(repo.HTMLURL() + "/src/" + url.PathEscape(string(refType)) + "/" + util.PathEscapeSegments(ref) + "/" + util.PathEscapeSegments(treePath))
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
|
@ -234,7 +235,7 @@ func GetContents(ctx context.Context, repo *repo_model.Repository, treePath, ref
|
|||
contentsResponse.HTMLURL = &htmlURLString
|
||||
contentsResponse.Links.HTMLURL = &htmlURLString
|
||||
|
||||
gitURL, err := url.Parse(fmt.Sprintf("%s/git/blobs/%s", repo.APIURL(), entry.ID.String()))
|
||||
gitURL, err := url.Parse(repo.APIURL() + "/git/blobs/" + url.PathEscape(entry.ID.String()))
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
|
|
|||
Loading…
Reference in a new issue